Pharmaceutical Packaging
Thermoform packaging market graphic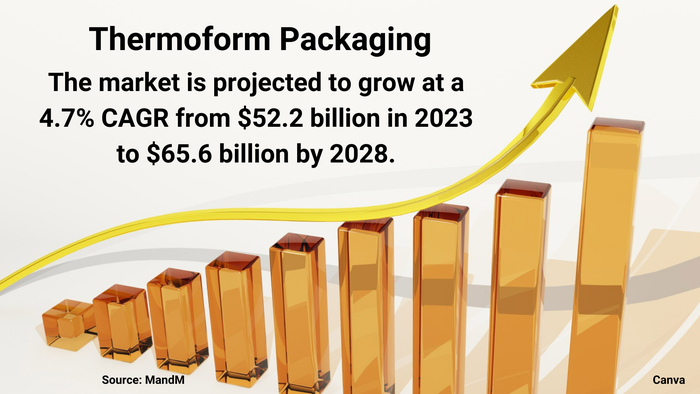
Packaging Design
Market Dynamics Favor Thermoform PackagingMarket Dynamics Favor Thermoform Packaging
Healthy demand from food and pharmaceutical companies will spur growth, despite sustainability challenges.
Sign up for the Packaging Digest News & Insights newsletter.